Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Last updated 16 maio 2024

Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

Privilege Escalation Attack and Defense Explained
“PACMAN” Hack Breaks Apple M1's Last Line of Defense - IEEE

Memory-based attacks increase as attackers dodge cloud defenses

Aqua Security Study Finds 1,400% Increase in Memory Attacks

Enterprise data breach: causes, challenges, prevention, and future

What is a Fileless Malware Attack (with examples)

Three flaws allow attackers to bypass UEFI Secure Boot feature

Types of Cyber Attacks You Should Be Aware of in 2024
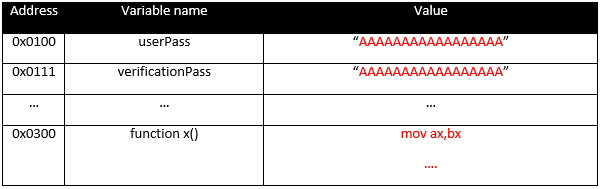
Inside the Mind of a Hacker: Attacking the Memory

Cyber Attack - an overview
Recomendado para você
-
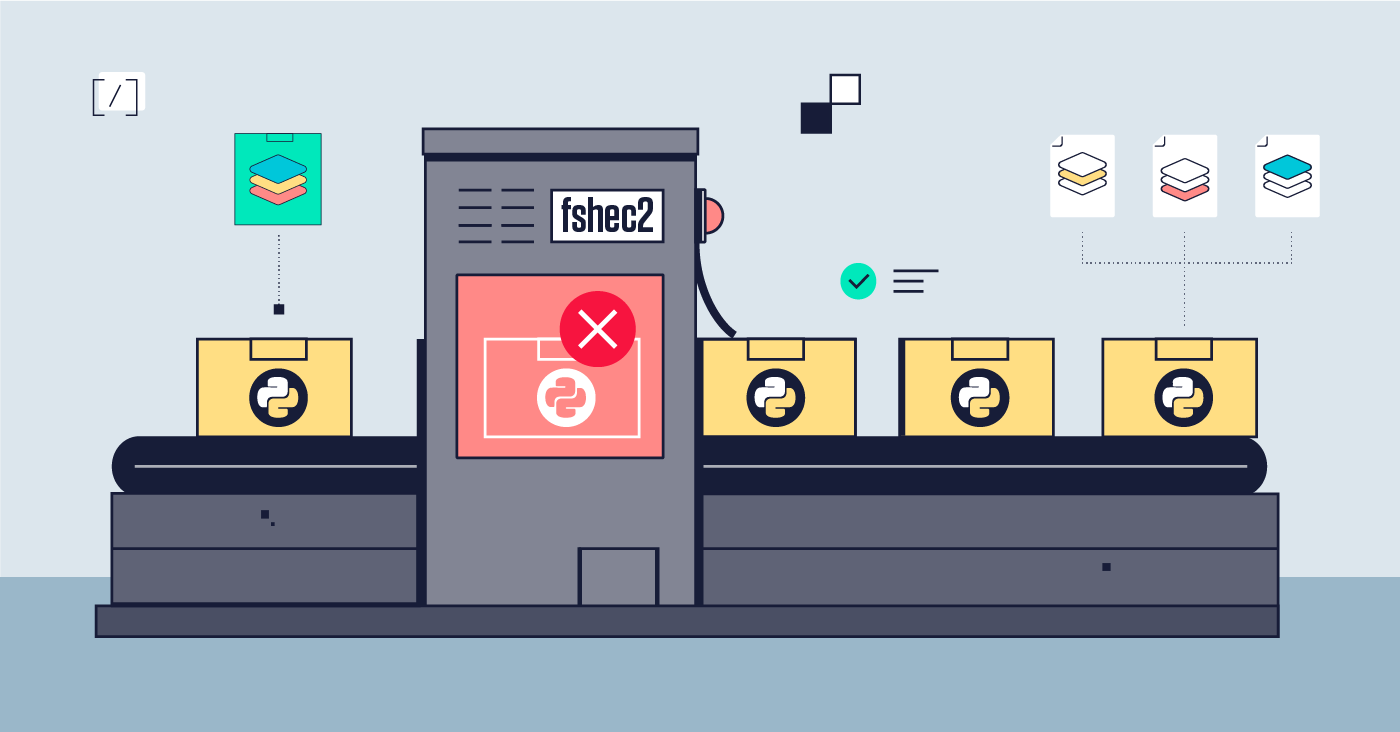 When byte code bites: Who checks the contents of compiled Python16 maio 2024
When byte code bites: Who checks the contents of compiled Python16 maio 2024 -
 ⚡️EVADE Script Pastebin 2022 AUTO FARM ⚡️ AUTO XP CASH ESP GOD16 maio 2024
⚡️EVADE Script Pastebin 2022 AUTO FARM ⚡️ AUTO XP CASH ESP GOD16 maio 2024 -
Evade-script/script at main · Lux11111111/Evade-script · GitHub16 maio 2024
-
 mobile script evade – ScriptPastebin16 maio 2024
mobile script evade – ScriptPastebin16 maio 2024 -
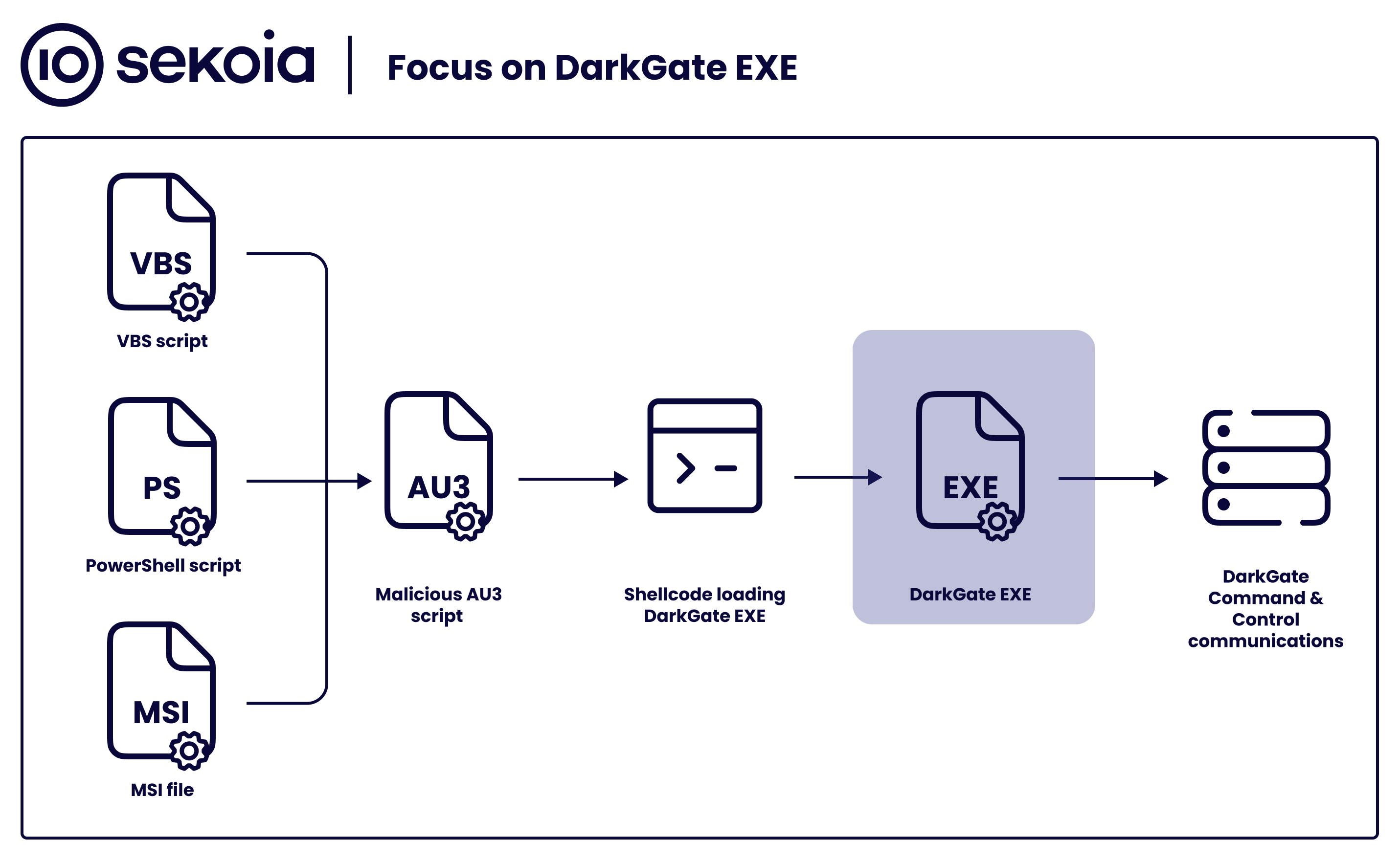
Sekoia.io on X: #DarkGate gained popularity among threat actors16 maio 2024
-
 Evade Script – Juninho Scripts16 maio 2024
Evade Script – Juninho Scripts16 maio 2024 -
 Evade Script Roblox: Auto Farm, Auto Respawn & More16 maio 2024
Evade Script Roblox: Auto Farm, Auto Respawn & More16 maio 2024 -
Winnti Hackers Split Cobalt Strike Into 154 Pieces To Evade Detection16 maio 2024
-
 Disassemble Script16 maio 2024
Disassemble Script16 maio 2024 -
 Evade Script - Summoner's Champion Information - League of Legends16 maio 2024
Evade Script - Summoner's Champion Information - League of Legends16 maio 2024
você pode gostar
-
 Ancient Tomb - Chapter 1 - Trailing Tartuccio and the Stag Lord - Walkthrough, Pathfinder: Kingmaker16 maio 2024
Ancient Tomb - Chapter 1 - Trailing Tartuccio and the Stag Lord - Walkthrough, Pathfinder: Kingmaker16 maio 2024 -
 Arcade1Up Star Wars Digital Pinball with Lit Marquee STW-P-10192 - Best Buy16 maio 2024
Arcade1Up Star Wars Digital Pinball with Lit Marquee STW-P-10192 - Best Buy16 maio 2024 -
 Vitoria Guimaraes vs Hajduk Split prediction, preview, team news16 maio 2024
Vitoria Guimaraes vs Hajduk Split prediction, preview, team news16 maio 2024 -
 Dragon Age: Origins Video Game Reviews and Previews PC, PS416 maio 2024
Dragon Age: Origins Video Game Reviews and Previews PC, PS416 maio 2024 -
 Pré-lista dos animes da Temporada de Inverno 201416 maio 2024
Pré-lista dos animes da Temporada de Inverno 201416 maio 2024 -
 Resenha ARTEMIS FOWL Livro X Filme16 maio 2024
Resenha ARTEMIS FOWL Livro X Filme16 maio 2024 -
 ArtStation - Cammy Street Fighter Lowpoly Rigged16 maio 2024
ArtStation - Cammy Street Fighter Lowpoly Rigged16 maio 2024 -
 O Segredo das bruxas antigas - Manuella Pedrão Lima Simões - Wattpad16 maio 2024
O Segredo das bruxas antigas - Manuella Pedrão Lima Simões - Wattpad16 maio 2024 -
 My Anime Goods on Tumblr16 maio 2024
My Anime Goods on Tumblr16 maio 2024 -
 Onde assistir ao vivo o jogo do Palmeiras hoje, domingo, 6; veja16 maio 2024
Onde assistir ao vivo o jogo do Palmeiras hoje, domingo, 6; veja16 maio 2024